Azure Well-Architected Framework: Building Reliable, Secure, Efficient Workloads
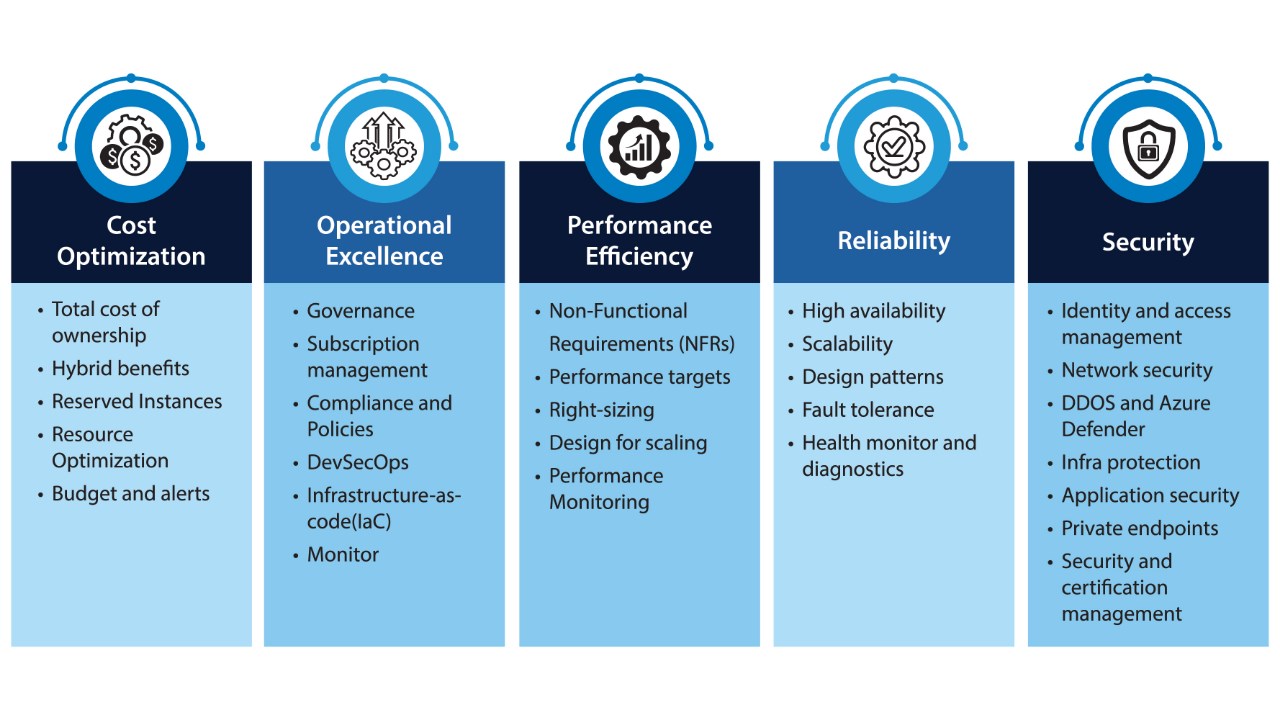
Azure Well-Architected Framework provides a holistic approach to designing, building, and maintaining cloud workloads that are resilient, secure, cost-effective, operationally sound, and performance optimized. It is structured around five core pillars—Reliability, Security, Cost Optimization, Operational Excellence, and Performance Efficiency—each offering a set of principles, maturity models, and design strategies to guide teams through the lifecycle of workload development and management.
🛠️ Reliability
Reliability is the foundation of workload continuity. It ensures that systems can withstand faults, recover gracefully, and maintain functionality under stress. The design principles begin with gathering business requirements that reflect the intended utility of the workload. These requirements must be documented and negotiated to align with investment and feasibility, driving technological decisions and operational strategies.
Resilience is a key tenet, emphasizing the need for fault tolerance against component failures, platform outages, and performance degradation. Systems should be designed to degrade gracefully rather than fail abruptly. Recovery readiness complements resilience by preparing workloads to anticipate and recover from failures with minimal disruption. This includes disaster preparedness and strategies for repairing corrupted data states.
Operational readiness is achieved by shifting left—testing failure conditions early in the development lifecycle. Shared visibility across teams, diagnostics, and alerts are essential for effective incident management and continuous improvement. Simplicity in design is also crucial; avoiding overengineering reduces the surface area for error, though care must be taken not to oversimplify and introduce single points of failure.
The reliability maturity model progresses from basic resilience to self-preservation, recovery readiness, stability maintenance, and ultimately sustained resilience. Key strategies include simplicity, critical flow analysis, failure mode evaluation, metric targeting, redundancy, scaling, self-preservation, testing, disaster recovery, and monitoring.
Reliability ensures workloads continue to function under stress, recover gracefully, and maintain consistent performance.
🔹 Maturity Model
| Level | Description |
|---|---|
| 1 | Get resilient |
| 2 | Self-preservation |
| 3 | Recovery readiness |
| 4 | Maintain stability |
| 5 | Stay resilient |
🔹 Key Design Strategies
- RE:01 Simplicity and efficiency
- RE:02 Critical flows
- RE:03 Failure mode analysis
- RE:04 Target metrics
- RE:05 Redundancy
- RE:06 Scaling
- RE:07 Self-preservation
- RE:08 Testing
- RE:09 Disaster recovery
- RE:10 Monitoring and alerting
🔐 Security
Security in Azure workloads is built on a zero-trust foundation, integrating the CIA triad—confidentiality, integrity, and availability—into every aspect of design and operation. A secure workload not only meets business goals but also resists attacks and mitigates the risk of breaches that could damage reputation and trust.
Security readiness begins with a plan that aligns with business priorities and defines responsibilities across the organization. This plan should integrate with reliability and operational strategies to ensure cohesive protection. Confidentiality is protected through access restrictions, data classification, and obfuscation techniques, ensuring that sensitive information remains within trusted boundaries.
Integrity safeguards the system against corruption in design, implementation, and operations. Controls must be in place to prevent tampering across all layers, from business logic to infrastructure. Availability is preserved through strong security controls that prevent downtime during incidents while maintaining data integrity and access for legitimate users.
Security posture must evolve continuously. Vigilance and improvement are necessary to stay ahead of evolving threats. Lessons from past incidents should inform future strategies, reducing detection time and improving containment.
The security maturity model advances from core security to threat prevention, risk assessment, system hardening, and advanced defense. Design strategies include establishing baselines, secure development lifecycles, threat analysis, segmentation, identity and access management, encryption, resource hardening, secret management, monitoring, testing, and incident response.
Security is built on a zero-trust model and integrates confidentiality, integrity, and availability (CIA triad) into every layer of the workload.
🔹 Maturity Model
| Level | Description |
|---|---|
| 1 | Core security |
| 2 | Threat prevention |
| 3 | Risk assessment |
| 4 | System hardening |
| 5 | Advanced defense |
🔹 Key Design Strategies
- SE:01 Security baseline
- SE:02 Secured development lifecycle
- SE:03 Threat analysis
- SE:04 Data classification
- SE:05 Segmentation
- SE:06 Identity and access management
- SE:07 Network controls
- SE:08 Encryption
- SE:09 Hardening resources
- SE:10 Application secrets
- SE:11 Monitoring and threat detection
- SE:12 Testing and validation
- SE:13 Incident response
💰 Cost Optimization
Cost optimization ensures that architectural decisions align with financial goals and deliver maximum return on investment. It begins with cultivating a cost-aware culture across teams, integrating budget tracking, reporting, and alignment with FinOps practices.
Designing with cost-efficiency means spending only on what is necessary to meet business objectives. Every decision—from technology selection to licensing and operations—has financial implications. Usage optimization focuses on maximizing the value of purchased features and continuously evaluating billing models to match actual usage.
Rate optimization allows teams to improve efficiency without
Cost Optimization ensures architectural decisions align with financial goals and deliver maximum ROI.
🔹 Maturity Model
| Level | Description |
|---|---|
| 1 | Cost ownership |
| 2 | Spend visibility |
| 3 | Signal integration |
| 4 | Production insights |
| 5 | Optimize at scale |
🔹 Key Design Strategies
- CO:01 Financial responsibility
- CO:02 Cost model
- CO:03 Cost data and reporting
- CO:04 Spending guardrails
- CO:05 Rate optimization
- CO:06 Usage and billing increments
- CO:07 Component costs
- CO:08 Environment costs
- CO:09 Flow costs
- CO:10 Data costs
- CO:11 Code costs
- CO:12 Scaling costs
- CO:13 Personnel time
- CO:14 Consolidation
⚙️ Operational Excellence
Operational Excellence centers on the practices and culture that ensure workloads are built, deployed, and maintained with precision, consistency, and minimal disruption. At its heart is the DevOps philosophy, which encourages collaboration between development and operations teams. This shared responsibility fosters a culture of continuous improvement, where diverse perspectives and skills converge to refine system design and operational processes.
Establishing development standards is essential to streamline productivity. By enforcing quality gates and systematic change management, teams can reduce friction and accelerate turnaround cycles from coding to testing. These standards should be right-sized—not overly rigid—but structured enough to drive consensus and maintain technical integrity.
Observability plays a pivotal role in evolving operations. Visibility into system behavior allows teams to derive insights and make informed decisions. Monitoring should span all pillars of the Well-Architected Framework, enabling both short-term fixes and long-term strategic planning. Data-driven improvements become the norm when observability is embedded into the culture.
Automation is another cornerstone of operational excellence. Replacing repetitive manual tasks with software automation increases consistency, reduces human error, and frees up valuable time. As workloads scale, automation becomes not just beneficial but essential.
Safe deployment practices ensure that changes to production are predictable and recoverable. By building modular and automated supply chains, teams can deploy confidently across environments. Guardrails and early testing help catch issues before they reach customers, preserving trust and stability.
The maturity model for Operational Excellence progresses from establishing a DevOps foundation to process standardization, release readiness, change management, and finally future adaptability. Key strategies include infrastructure as code, emergency response planning, instrumentation, task automation, and failure mitigation.
Operational Excellence focuses on DevOps practices, observability, and safe deployment to ensure workload quality and team cohesion.
🔹 Maturity Model
| Level | Description |
|---|---|
| 1 | DevOps foundation |
| 2 | Process standardization |
| 3 | Release readiness |
| 4 | Change management |
| 5 | Future adaptability |
🔹 Key Design Strategies
- OE:01 DevOps culture
- OE:02 Task execution process
- OE:03 Software development practices
- OE:04 Tools and processes
- OE:05 Infrastructure as code
- OE:06 Supply chain for workload development
- OE:07 Monitoring system
- OE:08 Instrument an application
- OE:09 Emergency response
- OE:10 Task automation
- OE:11 Automation design
- OE:12 Safe deployment practices
- OE:13 Failure mitigation
🚀 Performance Efficiency
Performance Efficiency is about making the most of your resources to deliver a responsive, scalable, and consistent user experience. It begins with negotiating realistic performance targets that align with business requirements. These targets should reflect not just technical metrics but also the expected impact on user experience across critical flows.
Meeting capacity requirements involves proactive measurement and baseline analysis. Even without full-scale performance testing, teams can identify potential bottlenecks and plan accordingly. This early insight lays the groundwork for sustainable performance management.
As workloads evolve, sustaining performance becomes a continuous effort. Changes in features, user behavior, and even optimizations in other architectural pillars can affect system performance. Teams must anticipate this variability and design systems that can adapt without degradation.
Long-term optimization is driven by real production data. Initial targets provide a starting point, but true efficiency comes from learning and adjusting based on actual usage patterns and platform evolution. Premature optimization can be wasteful; timing is key to maximizing impact.
The performance maturity model moves from setting targets to establishing baselines, incorporating signals, learning and adjusting, and finally tuning continuously. Design strategies include selecting appropriate services, scaling and partitioning, performance testing, optimizing code and infrastructure, and responding to live issues with agility.
Performance Efficiency ensures workloads use resources effectively to meet user demands and scale dynamically.
🔹 Maturity Model
| Level | Description |
|---|---|
| 1 | Set targets |
| 2 | Baseline metrics |
| 3 | Incorporate signals |
| 4 | Learn and adjust |
| 5 | Tune continuously |
🔹 Key Design Strategies
- PE:01 Performance targets
- PE:02 Capacity planning
- PE:03 Selecting services
- PE:04 Metrics and logs
- PE:05 Scaling and partitioning
- PE:06 Performance testing
- PE:07 Code and infrastructure
- PE:08 Data performance
- PE:09 Critical flows
- PE:10 Operational tasks
- PE:11 Live-issues responses
- PE:12 Continuous performance optimization